GWCTF 2019 re3
[GWCTF 2019]re3
ida64打开
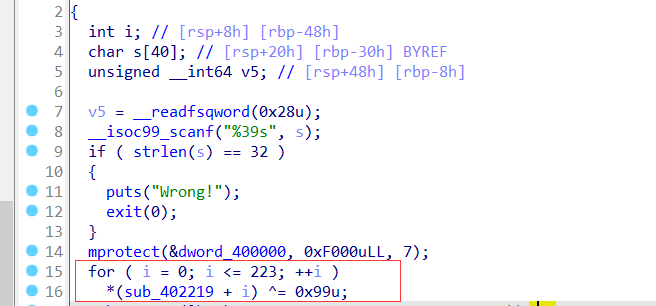
发现有SMC
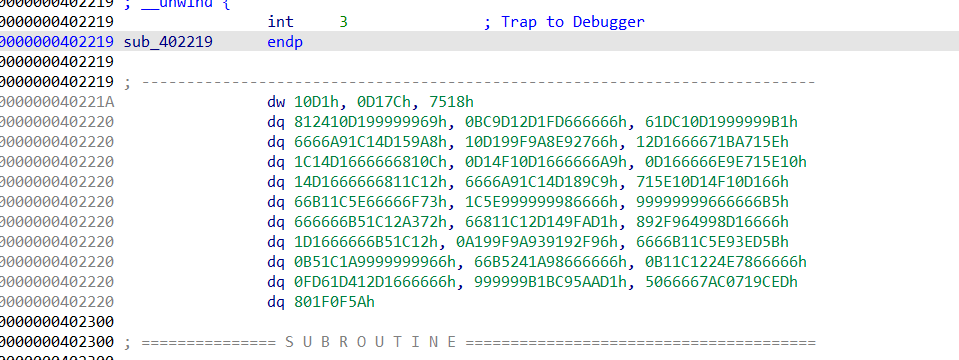
使用idc脚本解码
1 |
|
解码后再手动定义函数进行反汇编
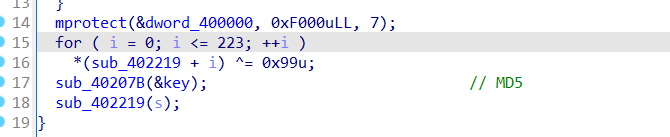
分析函数
sub_40207B
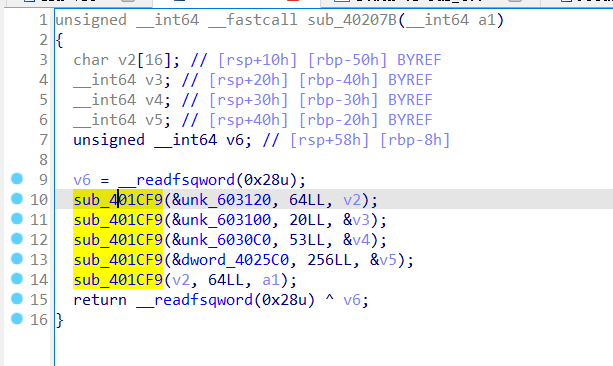
里面的sub_401CF9
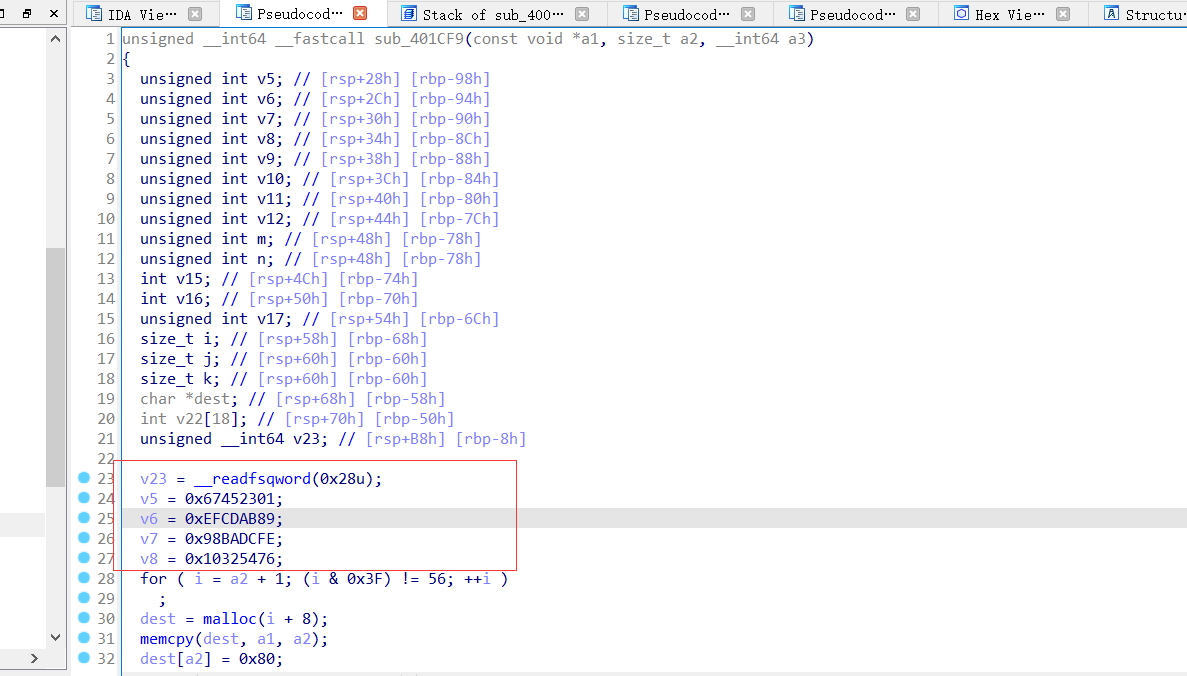
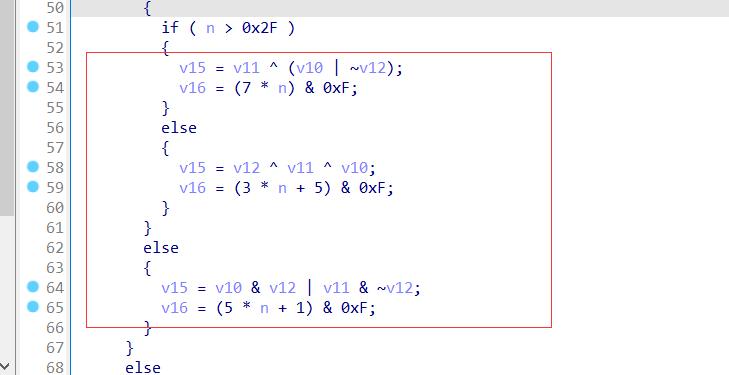
有MD5的标志数组加上线性函数
1 | F(X,Y,Z) = (X & Y) | ((~X) & Z); |
判断这是个MD5加密,动调获得结果
1 | CB8D493521B47A4CC1AE7E62229266 |
另一个函数则是AES,ECB模式的加密和一个判断
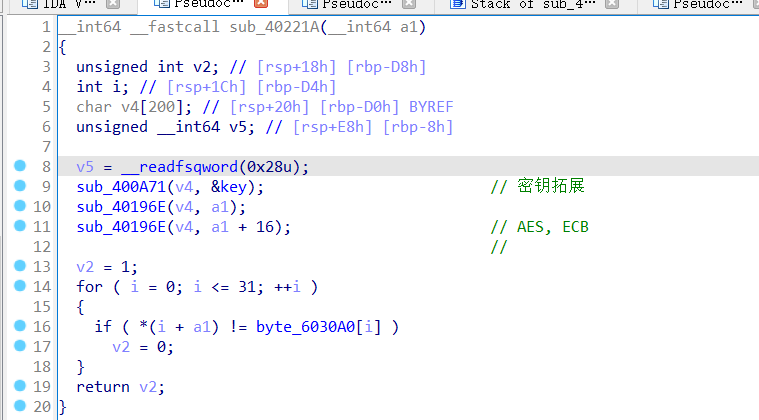
使用python脚本
1 | from Crypto.Cipher import AES |
1 | flag{924a9ab2163d390410d0a1f670} |